Twilio has upgraded their SSL certificate’s thumbprint algorithm to SHA256, your PHP/JAVA/ROR application which was able to send SMS/CALL before may not work unless you upgraded your certs to SHA2. You may need to all other SSL Errors without which you may not able to communicate with Twilio. We have listed down few common errors and steps to resolve them.
Reference link:
https://www.twilio.com/help/faq/december-ssl-certificate-update-prevents-twilio-api-access
Step-1
You can scan your website with SSL scanner ref. URL:
https://www.ssllabs.com/ssltest/
Scan report will give you the complete SSL information and errors. We have given few common errors and how you need to fix them…
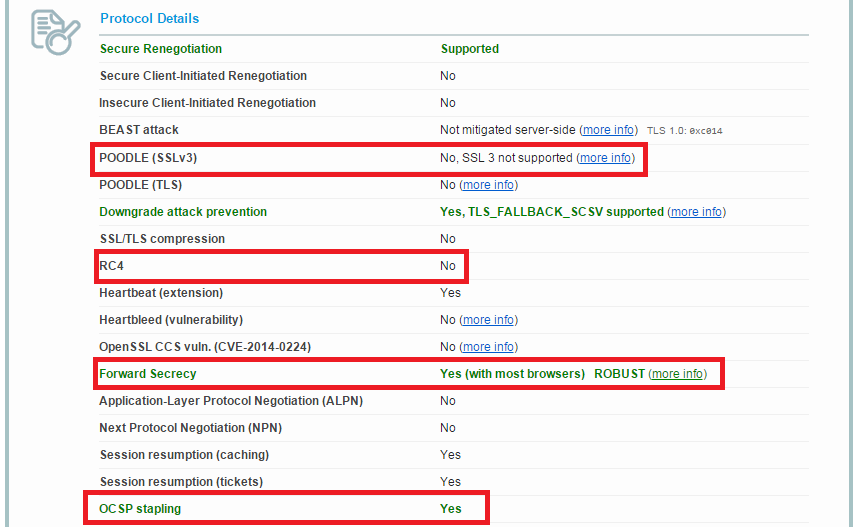
Errors as below
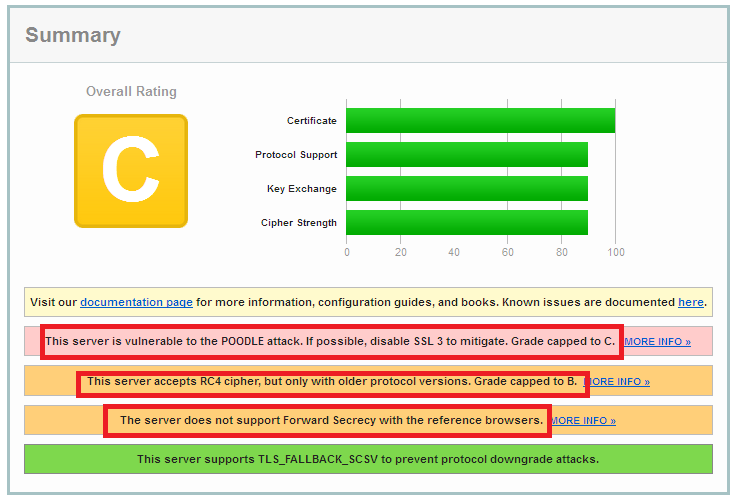
a. This server is vulnerable to the POODLE attack. If possible, disable SSL 3 to mitigate. Grade capped to C.
b. This server accepts RC4 cipher, but only with older protocol versions. Grade capped to B.
c. The server does not support Forward Secrecy with the reference browsers.
d. Enable OCSP stapling
Shown as below screenshot :

Step-2
Apply SSL error PATCH as shown below:
a. This server is vulnerable to the POODLE attack. If possible, disable SSL 3 to mitigate. Grade capped to C.
Fix: Modify below parameter in SSL configurations
/etc/apache2/mods-enabled/ssl.conf
SSLProtocol all -SSLv2 -SSLv3
b. This server accepts RC4 cipher, but only with older protocol versions. Grade capped to B.
c. The server does not support Forward Secrecy with the reference browsers.
Fix: Modify below parameter in apache virtualhost configurations
SSLHonorCipherOrder on
SSLCipherSuite “EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4”
d. Enable OCSP stapling
Fix: Enable OCSP stapling in Apache, add below configurations under VirtualHost tag /etc/apache2/sites-enabled/000-default.conf
#OCSP Stapling Settings
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLCACertificateFile /etc/apache2/ssl16/full_chain.pem (Combine site’s SSL and CA certificate and create a new full_chain.pem using below command)
#cat /etc/apache2/ssl/226cf6edd769a4cb.crt /etc/apache2/ssl/gd_bundle-g2-g1.crt >/etc/apache2/ssl/full_chain.pem
Enable Cache location for OCSP Stapling
Create a cache file in /var/run/ocsp
#touch /var/run/ocsp
add below parameter in /etc/apache2/sites-enabled/000-default.conf out side the VirtualHost tag
SSLStaplingCache shmcb:/var/run/ocsp(128000)
Do a configtest to check for Apache with SSL errors.
#apachectl -t
Once after configured all above configuration restart apache service
Validate OCSP Stapling configurations test using below command
#openssl s_client -connect www.example.com:443 -status -servername www.example.com
Step-3
Re-Run the SSL Scan report for your site https://www.ssllabs.com/ssltest/